首页/文章/游戏基址/软件逆向-DTrace 研究/
软件逆向-DTrace 研究
推荐 原创DTrace 研究
Windbg调试器单步异常,直接gn不处理。
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
32.0
: kd:x86> gn
The context
is
partially valid. Only x86 user
-
mode context
is
available.
WOW64 single step exception
-
code
4000001e
(first chance)
First chance exceptions are reported before
any
exception handling.
This exception may be expected
and
handled.
vmp3_6
+
0x4fa074
:
00000000
`
008fa074
90
nop
32.0
: kd:x86> ub
vmp3_6
+
0x4fa063
:
00000000
`
008fa063
33d3
xor edx,ebx
00000000
`
008fa065
ffca dec edx
00000000
`
008fa067
41
inc ecx
00000000
`
008fa068
84d9
test cl,bl
00000000
`
008fa06a
f7da neg edx
00000000
`
008fa06c
e91832f0ff jmp vmp3_6
+
0x3fd289
(
007fd289
)
00000000
`
008fa071
9d
popfd
00000000
`
008fa072
0f31
rdtsc
32.0
: kd:x86> gn
|
DTrace
使用D语言编写监控
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
|
#pragma D option quiet
#pragma D option destructive
syscall::Nt
*
:entry
/
execname
=
=
$
1
/
{
/
*
printf(
"%s [Caller %s]\n"
,probefunc, execname);
*
/
if
(probefunc
=
=
"NtQuerySystemInformation"
) {
if
(arg0
=
=
35
){
printf(
"Detect Kernel Debugger\n"
);
}
}
if
(probefunc
=
=
"NtQueryInformationProcess"
) {
if
(arg1
=
=
0x7
){
printf(
"Detect ProcessDebutPort\n"
);
}
if
(arg1
=
=
0x1E
){
printf(
"Detect ProcessDebugObjectHandle\n"
);
}
if
(arg1
=
=
0x1F
){
printf(
"Detect DebugFlags"
);
}
}
if
(probefunc
=
=
"NtSetInformationThread"
){
if
(arg1
=
=
0x11
){
printf(
"HideFromDebugger\n"
);
}
}
if
(probefunc
=
=
"NtQueryInformationProcess"
){
if
(arg1
=
=
0
){
printf(
"Query Process Basic Information \n"
);
}
}
if
(probefunc
=
=
"NtQueryObject"
){
if
(arg1
=
=
2
) {
printf(
"Query Object Type Information\n"
);
}
if
(arg1
=
=
3
) {
printf(
"Query Object Types Information\n"
);
}
}
if
(probefunc
=
=
"NtClose"
) {
printf(
"Close Handle : 0x%x\n"
,arg0);
}
if
(probefunc
=
=
"NtSetInformationObject"
) {
if
(arg1
=
=
4
){
printf(
"Set Handle Flag\n"
);
}
}
if
(probefunc
=
=
"NtGetContextThread"
){
printf(
"Get thread by thread handle : 0x%x"
,arg0);
}
if
(probefunc
=
=
"NtYieldExecution"
) {
printf(
"NtYieldExecution\n"
);
}
if
(probefunc
=
=
"DbgSetDebugFilterState"
) {
printf(
"DbgSetDebugFilterState\n"
);
}
}
|
效果发现其检测内核调试器的存在。
使用Dtrace进行追踪
|
1
|
dtrace.exe
-
s test.d vmp3.
6.exe
|
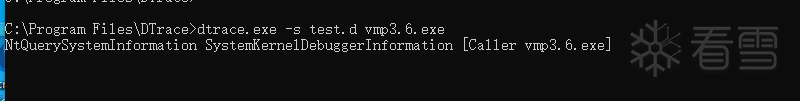
使用WinArk做inline hook。
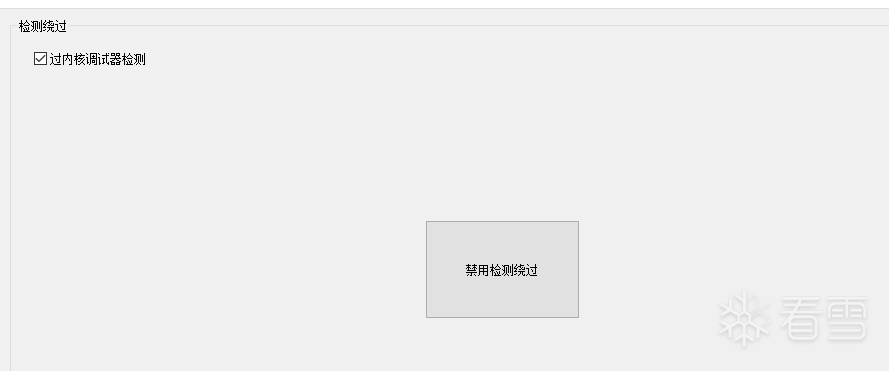
成功绕过vmp3.6 反内核调试器。
其他研究
|
1
2
3
4
5
6
7
8
|
0033
:
00000000
`
00e06169
48c7c101000000
mov rcx,
1
0033
:
00000000
`
00e06170
48c7c21b52e000
mov rdx,
0E0521Bh
0033
:
00000000
`
00e06177
ff1425d1c09a00 call qword ptr [
9AC0D1h
]
0033
:
00000000
`
00e0617e
cc
int
3
0033
:
00000000
`
00e0617f
488bc8
mov rcx, rax
0033
:
00000000
`
00e06182
ff142577c19a00 call qword ptr [
9AC177h
]
0033
:
00000000
`
00e06189
4883c428
add rsp,
28h
0033
:
00000000
`
00e0618d
cb retf
|
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
0
: kd> gn
The context
is
partially valid. Only x86 user
-
mode context
is
available.
WOW64 single step exception
-
code
4000001e
(first chance)
First chance exceptions are reported before
any
exception handling.
This exception may be expected
and
handled.
00000000
`
00528bd5
e948073800 jmp
008a9322
32.0
: kd:x86> gn
The context
is
partially valid. Only x86 user
-
mode context
is
available.
WOW64 single step exception
-
code
4000001e
(first chance)
First chance exceptions are reported before
any
exception handling.
This exception may be expected
and
handled.
00000000
`
0052a6b6
e98dee3700 jmp
008a9548
32.0
: kd:x86> gn
The context
is
partially valid. Only x86 user
-
mode context
is
available.
WOW64 single step exception
-
code
4000001e
(first chance)
First chance exceptions are reported before
any
exception handling.
This exception may be expected
and
handled.
00000000
`
00529a6a
e9f7f93700 jmp
008a9466
32.0
: kd:x86> gn
The context
is
partially valid. Only x86 user
-
mode context
is
available.
WOW64 single step exception
-
code
4000001e
(first chance)
First chance exceptions are reported before
any
exception handling.
This exception may be expected
and
handled.
00000000
`
00527c85
e9c6153800 jmp
008a9250
32.0
: kd:x86> gn
|
更多【DTrace 研究】相关视频教程:www.yxfzedu.com
相关文章推荐
- 软件逆向-WinCHM 再探索! - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-DTrace 研究 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-常见语言基础逆向方法合集 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-分享个东西,cheat engine的变速精灵(speedhack)模块调用方法. - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-SoftAny WinCHM 5.496 注册码笔记 by ZeNiX - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-crackme001 Acid burn - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-定制bcc/ebpf在android平台上实现基于dwarf的用户态栈回溯 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-Java安全小白的入门心得 - 初见RMI协议 - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-这个崩溃有点意思,你中过招吗 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-PE头解析-字段说明 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-PE加载过程 FileBuffer-ImageBuffer - 游戏基址二进制漏洞 密码应用智能设备
- 加壳脱壳-进程 Dump & PE unpacking & IAT 修复 - Windows 篇 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-第五空间 crackme深度分析 - 游戏基址二进制漏洞 密码应用智能设备
- Pwn-DAS9月月赛PWN题出题心路 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-CSAW-CTF-Web部分题目 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-2022MT-CTF Re - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-逆向IoRegisterPlugPlayNotification获取即插即用回调地址,配图加注释超级详细 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-针对百度旗下的一个会议软件,简单研究其CEF框架 - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-逆向篇三:解决Flutter应用不能点击问题 - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-Android - 系统级源码调试 - 游戏基址二进制漏洞 密码应用智能设备
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多