360壳,随便脱一下就行了。
先查尔斯抓个包看看
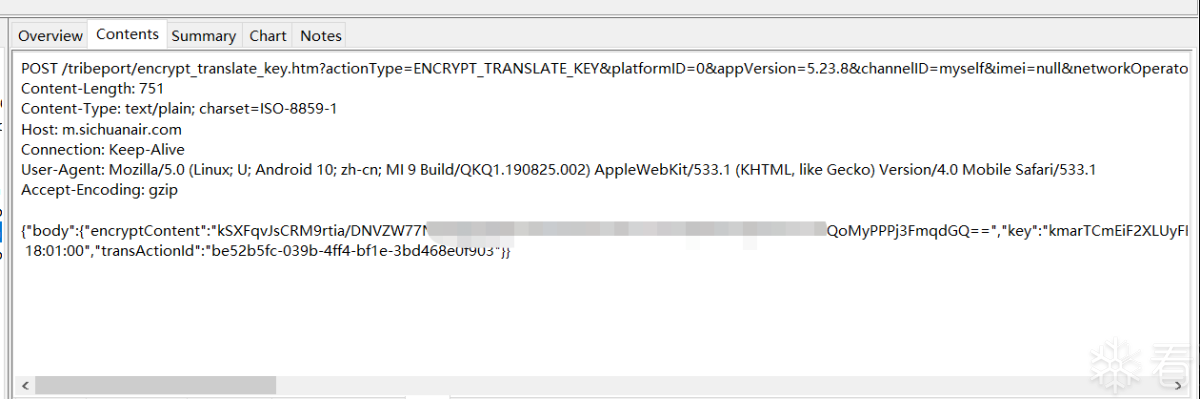
都被加密了,可以看到,报文中有个sign字段,那就直接dex拖jadx里,直接搜sign,看到了 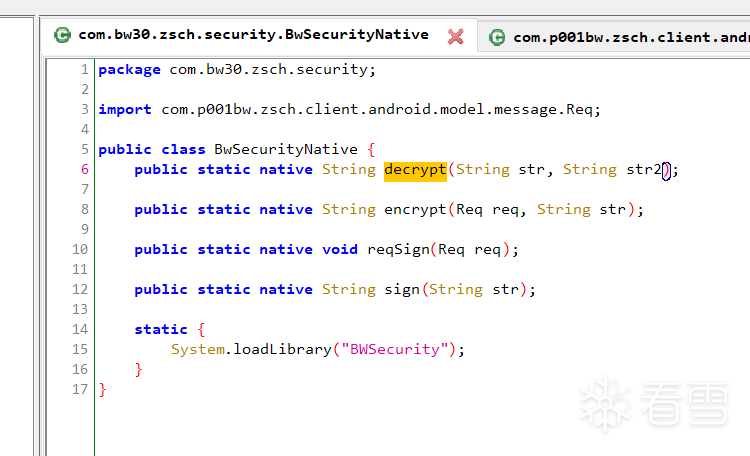
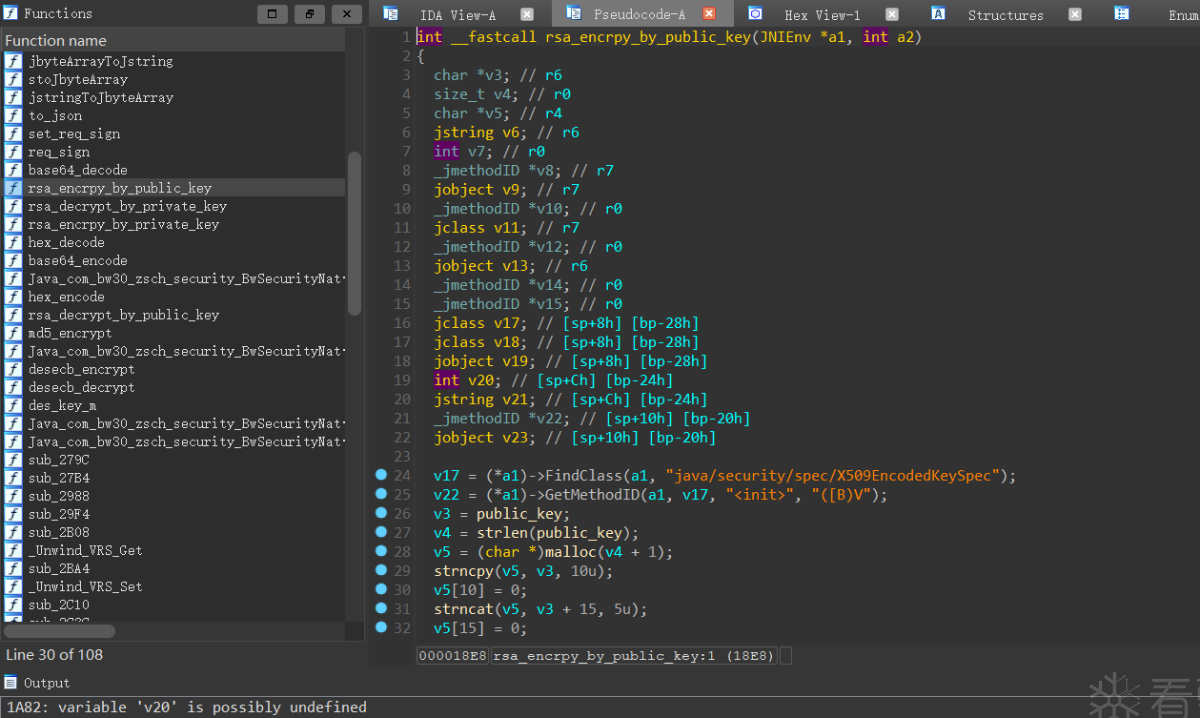
几个方法hook一下后发现是
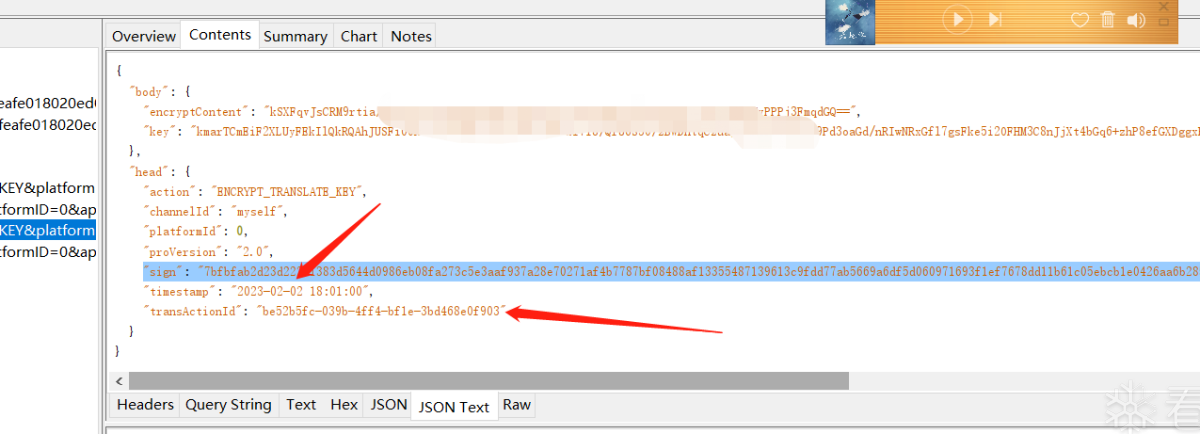
取了timestamp的年月日+transActionId+字符串"2822563730"拼接后的MD5也就是2023-02-02be52b5fc-039b-4ff4-bf1e-3bd468e0f9032822563730
MD5后为:c2018b299df789241f92552c248289bd
然后RSA加密公钥为: 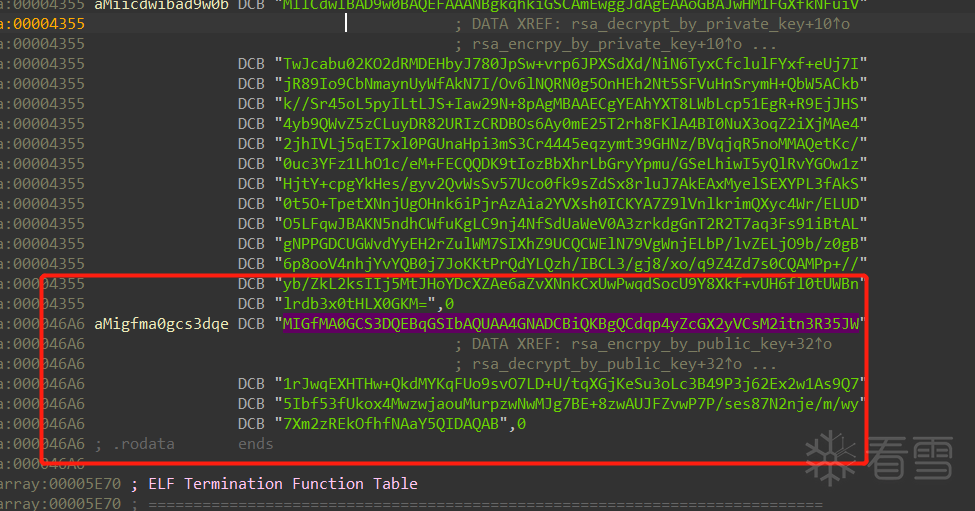 也就是"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCdqp4yZcGX2yVCsM2itn3R35JW1rJwqEXHTHw+QkdMYKqFUo9svO7LD+U/tqXGjKeSu3oLc3B49P3j62Ex2w1As9Q75Ibf53fUkox4MwzwjaouMurpzwNwMJg7BE+8zwAUJFZvwP7P/ses87N2nje/m/wy7Xm2zREkOfhfNAaY5QIDAQAB"
也就是"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCdqp4yZcGX2yVCsM2itn3R35JW1rJwqEXHTHw+QkdMYKqFUo9svO7LD+U/tqXGjKeSu3oLc3B49P3j62Ex2w1As9Q75Ibf53fUkox4MwzwjaouMurpzwNwMJg7BE+8zwAUJFZvwP7P/ses87N2nje/m/wy7Xm2zREkOfhfNAaY5QIDAQAB"
然后加密一下看看
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
materialButton.setOnClickListener(new View.OnClickListener() {
public void onClick(View view) {
String key
=
"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCdqp4yZcGX2yVCsM2itn3R35JW1rJwqEXHTHw+QkdMYKqFUo9svO7LD+U/tqXGjKeSu3oLc3B49P3j62Ex2w1As9Q75Ibf53fUkox4MwzwjaouMurpzwNwMJg7BE+8zwAUJFZvwP7P/ses87N2nje/m/wy7Xm2zREkOfhfNAaY5QIDAQAB"
;
String res
=
null;
try
{
res
=
a(
"c2018b299df789241f92552c248289bd"
,key);
} catch (Exception e) {
e.printStackTrace();
}
Log.d(
"MainActivity"
,res);
}
});
}
@RequiresApi
(api
=
Build.VERSION_CODES.O)
public static String a(String
str
, String str2) throws Exception {
Cipher v1
=
Cipher.getInstance(
"RSA"
);
v1.init(
1
, KeyFactory.getInstance(
"RSA"
).generatePublic(new X509EncodedKeySpec(Base64.getDecoder().decode(str2))));
return
Base64.getEncoder().encodeToString(v1.doFinal(
str
.getBytes()));
}
|
看一眼日志:
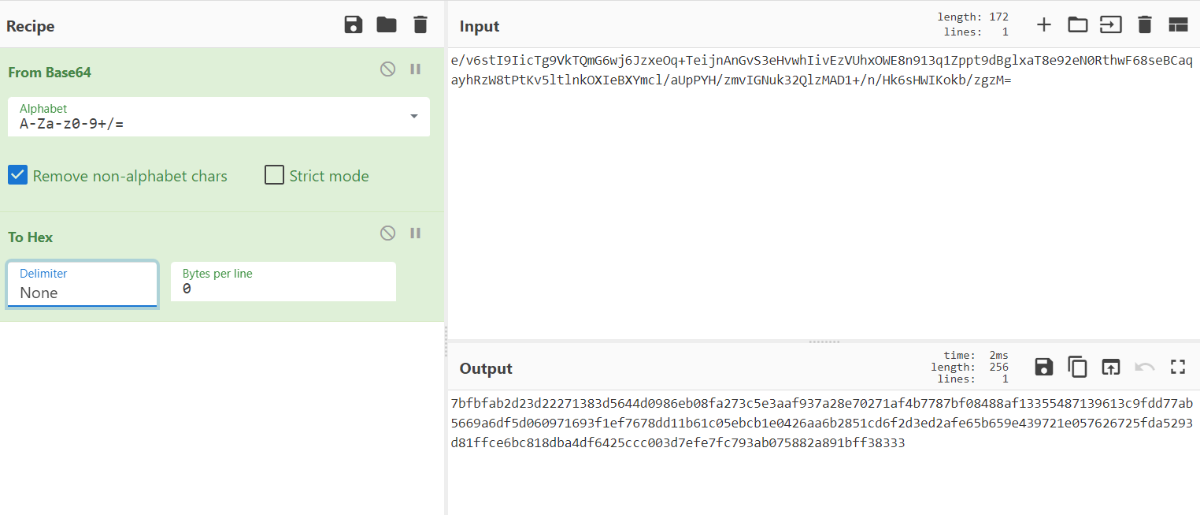
2023-02-06 13:08:53.592 6946-6946/com.bangcle.myapplication D/MainActivity: e/v6stI9IicTg9VkTQmG6wj6JzxeOq+TeijnAnGvS3eHvwhIivEzVUhxOWE8n913q1Zppt9dBglxaT8e92eN0RthwF68seBCaqayhRzW8tPtKv5ltlnkOXIeBXYmcl/aUpPYH/zmvIGNuk32QlzMAD1+/n/Hk6sHWIKokb/zgzM=
然后看一下sign:"sign": "7bfbfab2d23d22271383d5644d0986eb08fa273c5e3aaf937a28e70271af4b7787bf08488af13355487139613c9fdd77ab5669a6df5d060971693f1ef7678dd11b61c05ebcb1e0426aa6b2851cd6f2d3ed2afe65b659e439721e057626725fda5293d81ffce6bc818dba4df6425ccc003d7efe7fc793ab075882a891bff38333",
那直接base64解密一下hex一下就是了。
更多【四川航空sign分析】相关视频教程:www.yxfzedu.com




 也就是"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCdqp4yZcGX2yVCsM2itn3R35JW1rJwqEXHTHw+QkdMYKqFUo9svO7LD+U/tqXGjKeSu3oLc3B49P3j62Ex2w1As9Q75Ibf53fUkox4MwzwjaouMurpzwNwMJg7BE+8zwAUJFZvwP7P/ses87N2nje/m/wy7Xm2zREkOfhfNAaY5QIDAQAB"
也就是"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCdqp4yZcGX2yVCsM2itn3R35JW1rJwqEXHTHw+QkdMYKqFUo9svO7LD+U/tqXGjKeSu3oLc3B49P3j62Ex2w1As9Q75Ibf53fUkox4MwzwjaouMurpzwNwMJg7BE+8zwAUJFZvwP7P/ses87N2nje/m/wy7Xm2zREkOfhfNAaY5QIDAQAB"