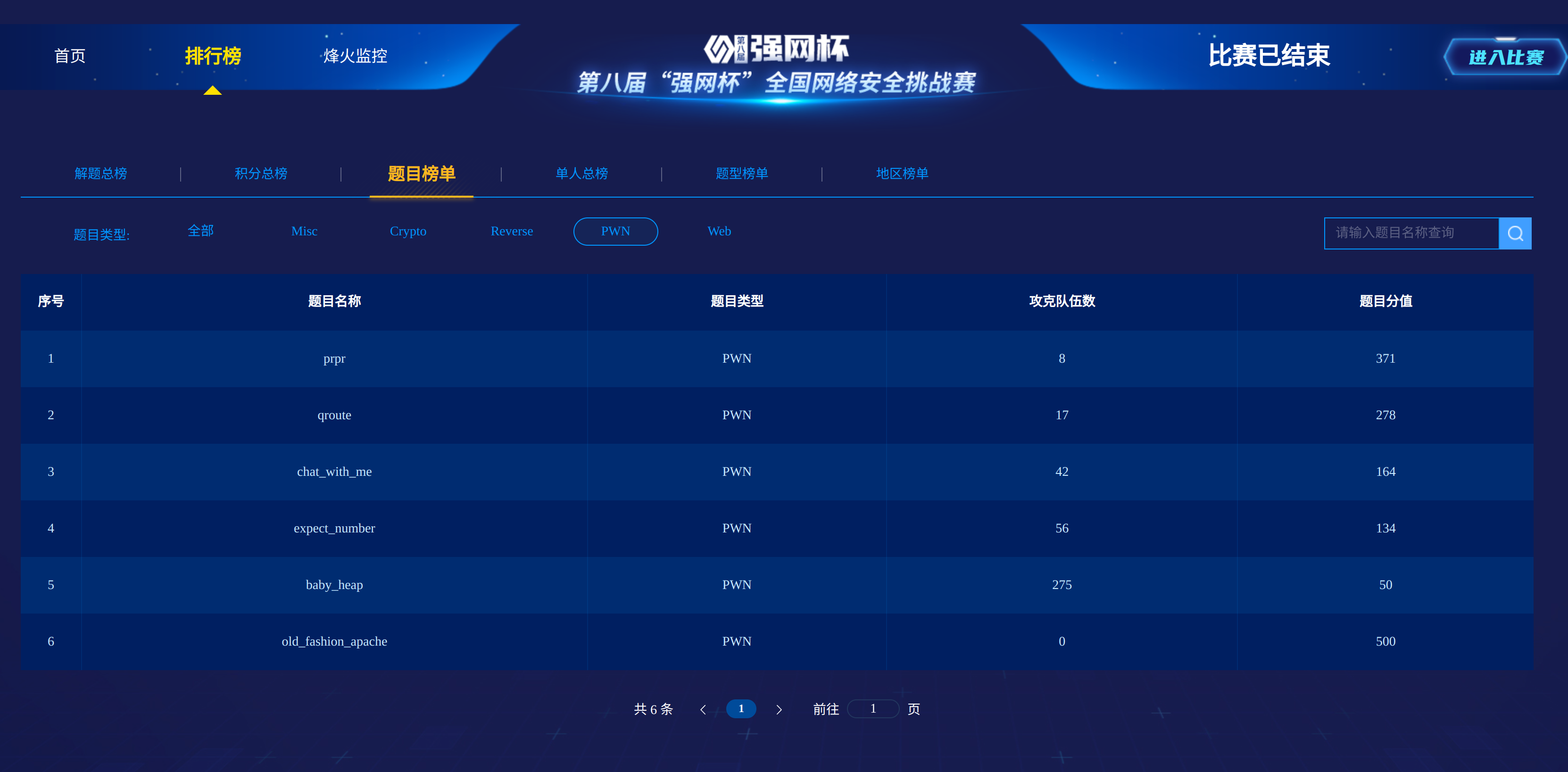
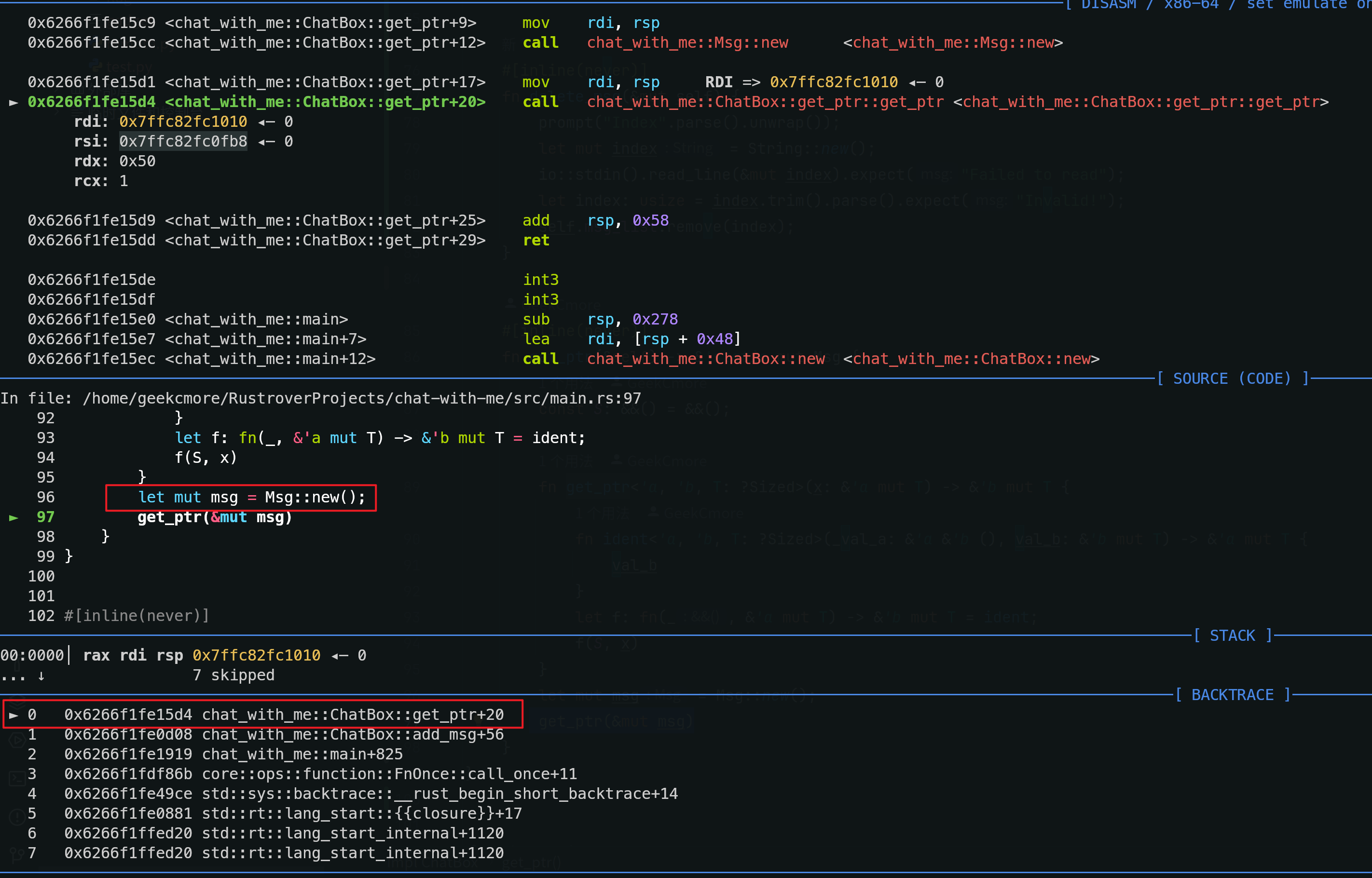
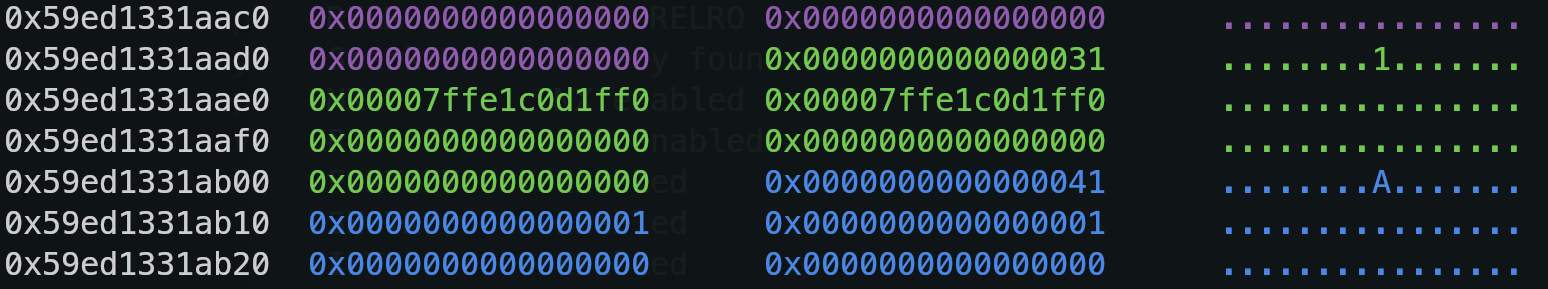
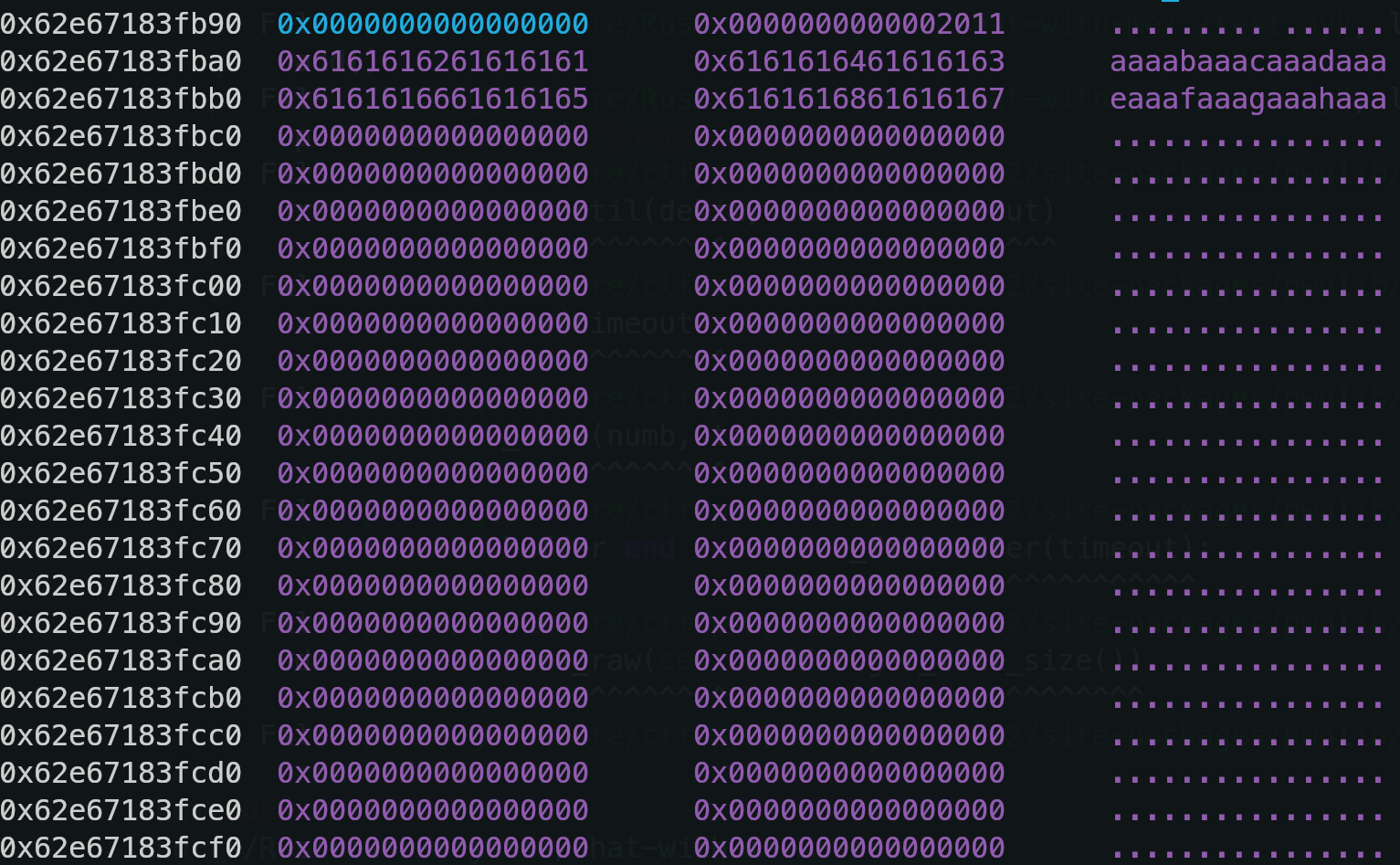
Pwn-强网杯S8 Rust Pwn chat-with-me出题思路分享
推荐 原创更多【Pwn-强网杯S8 Rust Pwn chat-with-me出题思路分享】相关视频教程:www.yxfzedu.com
相关文章推荐
- java-【TiDB】TiDB CLuster部署 - 其他
- tidb-KCC@广州与 TiDB 社区联手—广州开源盛宴 - 其他
- pdf-耗时3年写了一本数据结构与算法pdf!开源了 - 其他
- 计算机外设-键盘win键无法使用,win+r不生效、win键没反应、Windows键失灵解决方案(亲测可以解决) - 其他
- 计算机外设-键盘打字盲打练习系列之认识键盘——0 - 其他
- 机器学习-Azure 机器学习 - 有关为 Azure 机器学习配置 Kubernetes 群集的参考 - 其他
- 信息可视化-ESP32网络开发实例-将数据保存到InfluxDB时序数据库 - 其他
- 计算机外设-基于QT使用OpenGL,加载obj模型,进行鼠标交互 - 其他
- 前端框架-React进阶之路(三)-- Hooks - 其他
- 运维-python实现炒股自动化,个人账户无门槛量化交易的开始 - 其他
- 网络-各大电商平台API接口调用,对接拼多多开放平台API接口获得商品详情实时数据演示 - 其他
- r语言-gpt支持json格式的数据返回(response_format: ‘json_object‘) - 其他
- pdf-pdf.js不分页渲染(渲染完整内容) - 其他
- 自动驾驶-自动驾驶学习笔记(八)——路线规划 - 其他
- pdf-Word转PDF简单示例,分别在windows和centos中完成转换 - 其他
- spring boot-java 企业工程管理系统软件源码+Spring Cloud + Spring Boot +二次开发+ MybatisPlus + Redis - 其他
- python-利用 Google Artifact Repository 构建maven jar 存储仓库 - 其他
- python-PyCharm因安装了illuminated Cloud插件导致加载项目失败 - 其他
- list-list复制出新的list后修改元素,也更改了旧的list? - 其他
- 语言模型-论文导读 | 融合大规模语言模型与知识图谱的推理方法 - 其他
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多
- java-一个轻量级 Java 权限认证框架——Sa-Token
- 运维-RK3568平台 查看内存的基本命令
- 算法-深入理解强化学习——多臂赌博机:梯度赌博机算法的数学证明
- apache-Apache Doris 是什么
- list-Redis数据结构七之listpack和quicklist
- css-HTML CSS JS 画的效果图
- python-Win10系统下torch.cuda.is_available()返回为False的问题解决
- python-定义无向加权图,并使用Pytorch_geometric实现图卷积
- git-如何使用git-credentials来管理git账号
- prompt-Anaconda Powershell Prompt和Anaconda Prompt的区别